February 9th, 2026
Release Date: 2026-02-09
Status: Production Ready
Overview
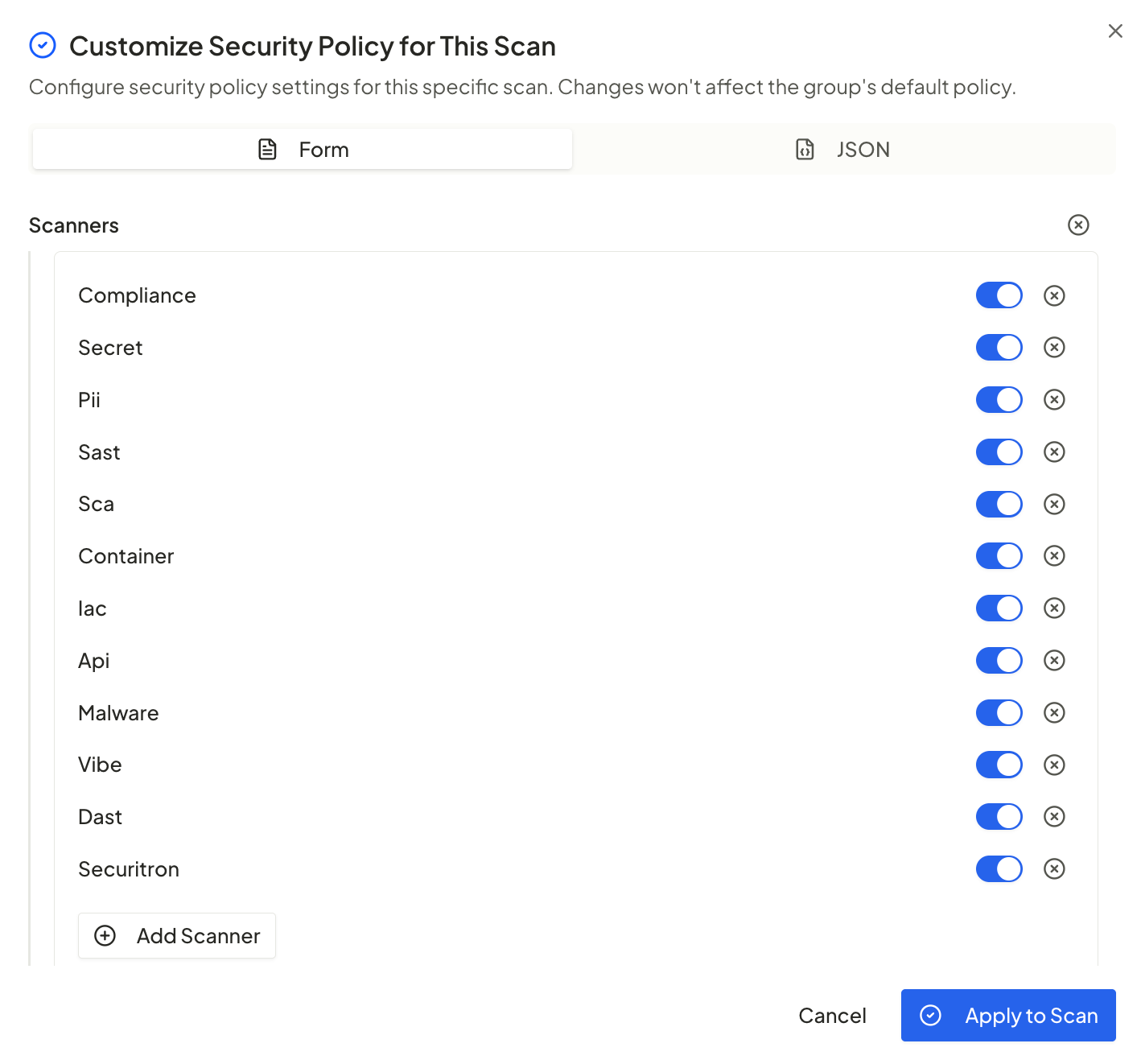
This release introduces scan-level custom security policies, enabling teams to override group-level security configurations on a per-scan basis. This enhancement provides greater flexibility for projects that require tailored security controls without modifying shared group policies.
Key Highlights
Define custom security policies per scan
Override group policies only when needed
Automatically preserve custom policies during rescans
Support for both form-based and JSON-based policy editing
Plan-based enforcement ensures all policies comply with subscription tier limits
What’s New
New UI to configure scan-level security policies at scan creation
Workers automatically prioritize custom policies over group defaults
Rescans inherit the original scan’s policy configuration
Custom policies are visible in scan metadata for transparency
Compatibility
Fully backward compatible
No breaking API changes
Default behavior remains unchanged if no custom policy is defined
January 21st, 2026
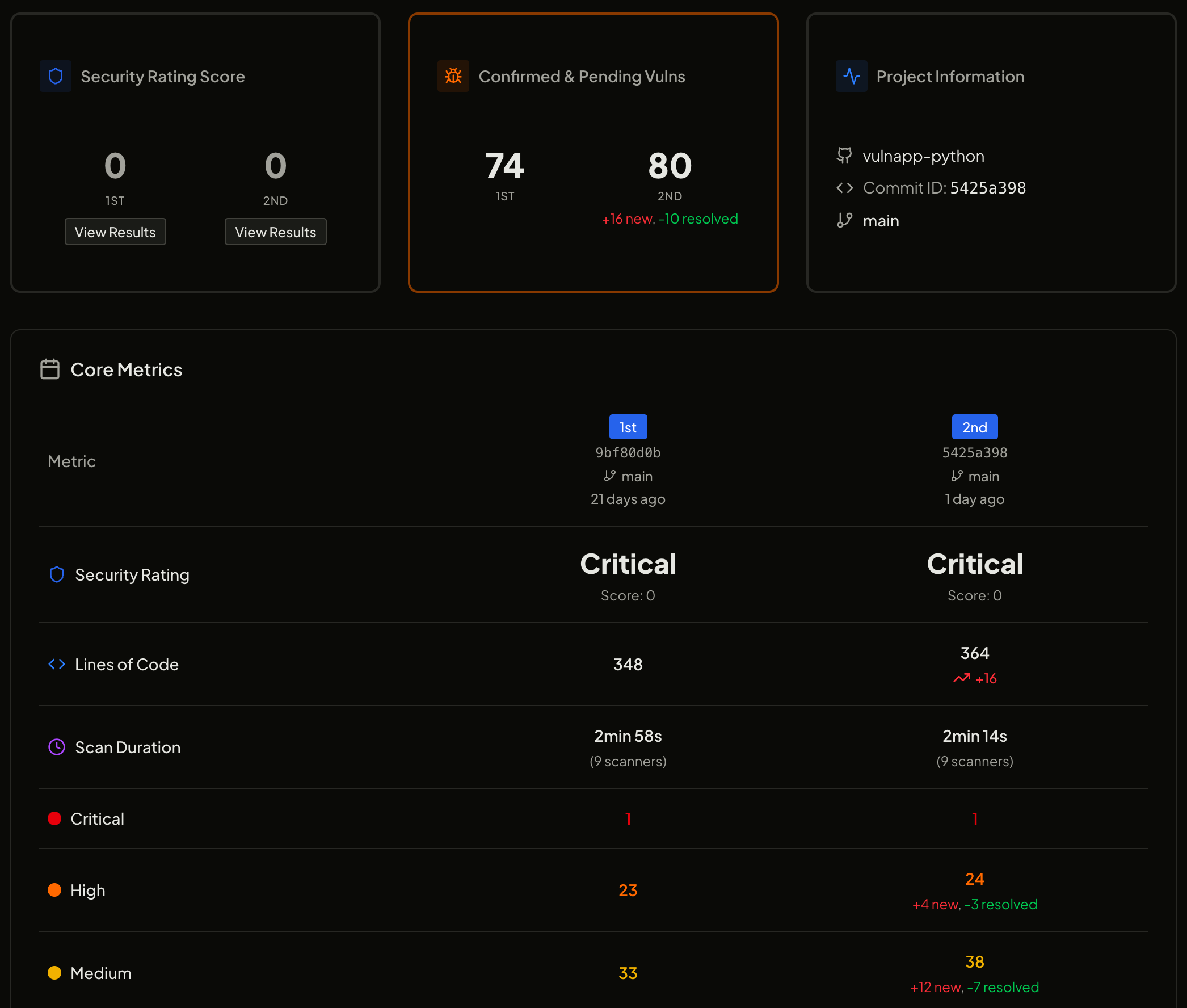
AquilaX now supports scan comparison, allowing teams to compare two security scans (e.g., across commits or branches) and view:
New vulnerabilities introduced
Vulnerabilities resolved
Changes in severity distribution
Scanner-specific deltas
Key Benefits
Track security trends: Understand if security posture is improving or regressing over time.
Validate remediations: Confirm that fixed vulnerabilities no longer appear in later scans.
Detect regressions early: Identify security issues introduced by recent code changes.
Integrate into CI/CD: Enforce policies based on delta (e.g., block builds if new critical vulns are found).
This feature supports all scan types including SAST, SCA, Secrets, IaC, and Compliance.
January 7th, 2026
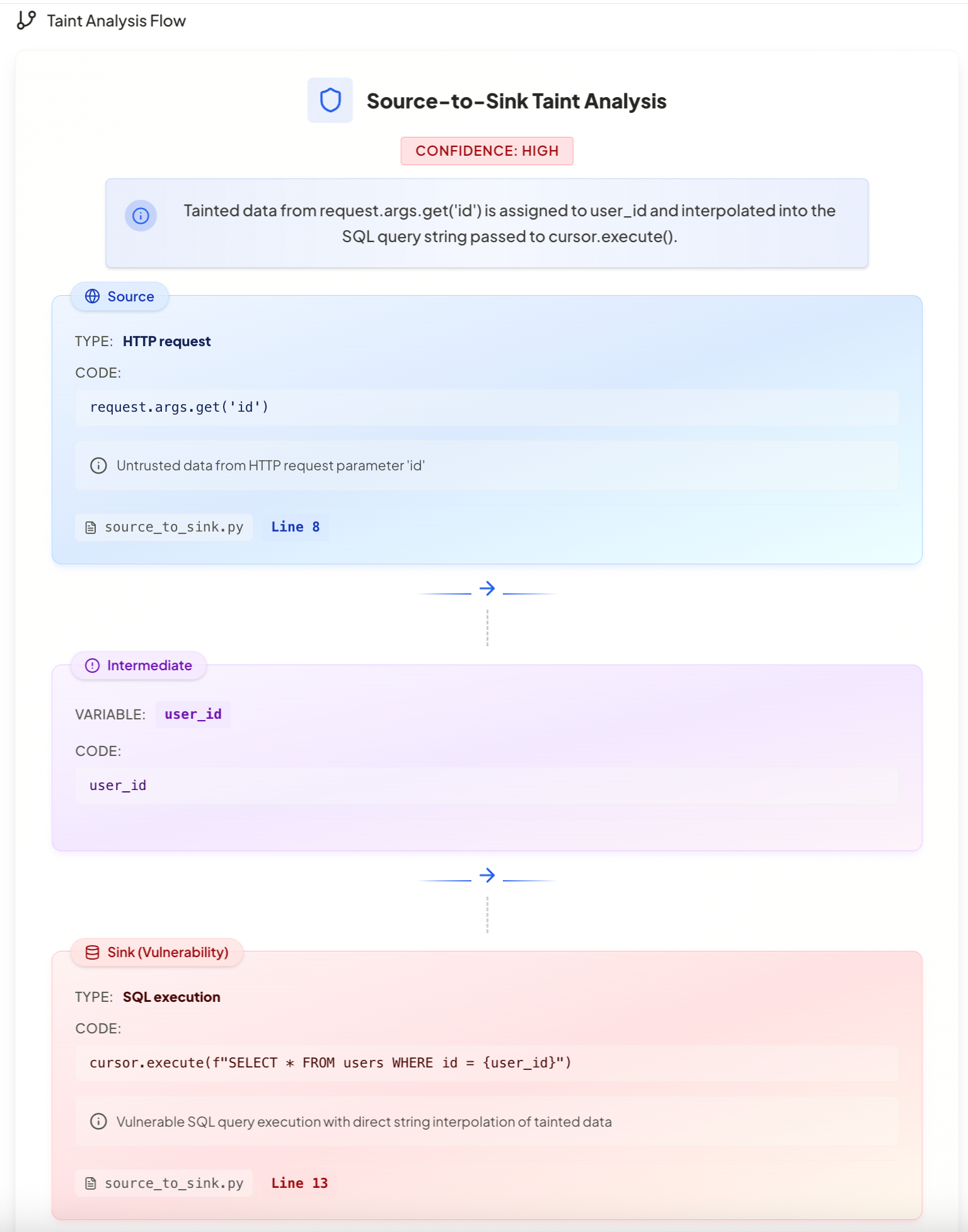
AquilaX now supports Source-to-Sink analysis in both multi-tenant and single-tenant deployments for its SAST findings.
This feature allows users to trace data flow from the initial point of injection (source) all the way to the vulnerable function (sink). By following this path, developers can visualize the exact journey of potentially harmful data, making it easier to pinpoint where the vulnerability originates—and more importantly, where it can be fixed.
December 1st, 2025
What’s included
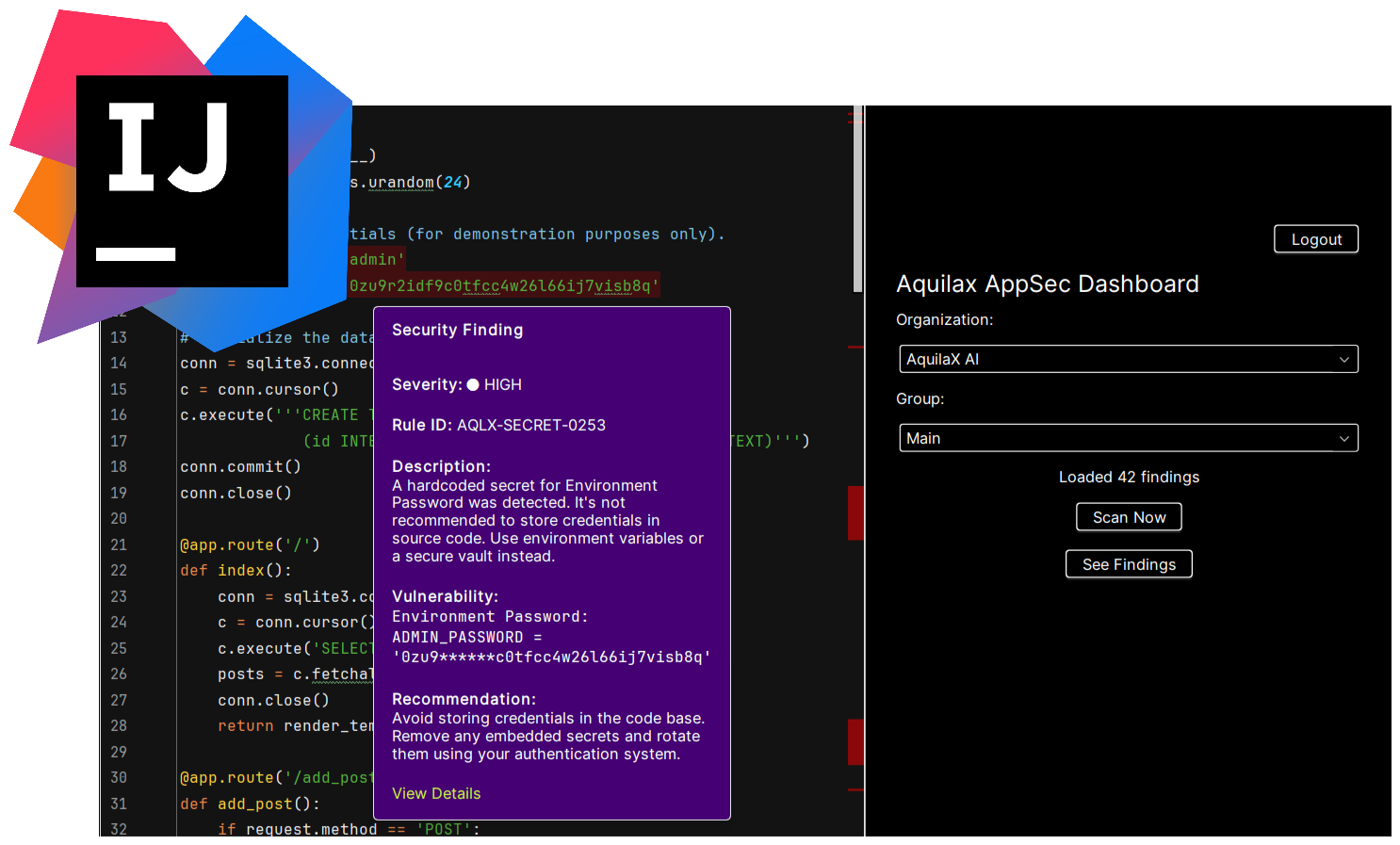
Real-time security analysis: As you code in IntelliJ IDEA, the plugin runs security analysis and surfaces potential vulnerabilities immediately.
In-editor highlighting: Vulnerable code segments (true positives and unverified findings) are visually marked directly in your source files.
Integrated tool window / dashboard: A dedicated “AquilaX AppSec” panel lets you manage organizations, groups, and trigger scans, without leaving the IDE.
Automated scanning from within IDE: You can start scans manually from the IDE, monitor progress, and cancel if needed.
Findings summary & detailed reports: Once scans finish, you can fetch findings inside the IDE; the plugin displays severity, rule IDs, descriptions, remediation suggestions.
Seamless link to web dashboard: For more in-depth analysis and history, each finding includes a direct link to the full report in the AquilaX web dashboard.
Project-wide visibility: Files containing security issues get error markers in the project view, allowing quick identification of which files need attention.
How to install
Available via JetBrains Marketplace (search “AquilaX AppSec”) — install and restart IDE.
Or: manual install using the plugin ZIP via “Install Plugin from Disk” if you downloaded it from releases.
Typical workflow from inside IDE
Open the “AquilaX AppSec” tool window after installation.
Authenticate — either via browser-based login or via Personal Access Token (PAT).
Select organization and project group context.
Trigger a scan (“Scan Now”) — status updates inside IDE, and you may cancel if needed.
When done, fetch findings. Plugin shows summary; number of findings appears in status bar.
In your source files: vulnerable code is highlighted (red = confirmed true positives; orange = unverified), with hover-tooltips providing severity, rule ID, description, code snippet, remediation advice, and a link to the web report.
Project view marks files containing issues to help you quickly navigate.
November 22nd, 2025

Overview
This release introduces Unified Security Reporting, a major enhancement that consolidates multiple industry-standard security classifications into a single, consistent reporting framework within AquilaX. The update improves visibility, reduces fragmentation across tools, and accelerates vulnerability triage and remediation workflows.
Key Features
✔ Unified Report View
All supported security frameworks are now available in one centralized dashboard, including:
OWASP Top 10
CWE Top 25
CVE Exposure
PCI DSS Alignment
Each finding shows its mapped classifications, technical evidence, severity scoring, and remediation guidance.
✔ Automated Classification Mapping
AquilaX automatically correlates findings and applies cross-framework mappings:
CVE → CWE → OWASP
Code-level finding → CWE structural weakness
Control-level finding → PCI DSS requirement
This enables engineers to quickly understand root causes and compliance impact.
✔ Normalized Severity Model
Findings coming from multiple scanners now follow a unified severity scale.
This reduces inconsistent scoring and helps teams prioritize more effectively.
✔ Deduplication Engine
The system identifies and merges duplicate issues across static analysis, dependency scanning, runtime monitoring, and configuration checks.
This ensures one issue = one source of truth.
✔ Export Support
Unified reports can now be exported in:
JSON (API + CLI)
PDF
CSV
Extended SBOM formats
Exports preserve complete classification mappings and traceability back to the originating scanner.
Why This Matters
Modern security pipelines generate findings from numerous independent tools. Without consolidation, teams face duplicated data, varied severities, and manual interpretation overhead.
This release eliminates these challenges by delivering a single, coherent security posture overview for the entire application lifecycle.
Additional Improvements
Performance optimizations to reduce report loading times
Improved mapping engine for mixed-language repositories
Updated compliance schemas for PCI DSS v4.0
Extended dependency graph resolution for polyglot builds
Availability
This feature is now available for:
Ultimate Tier customers
All deployment modes (cloud, hybrid, and on-prem)
November 14th, 2025
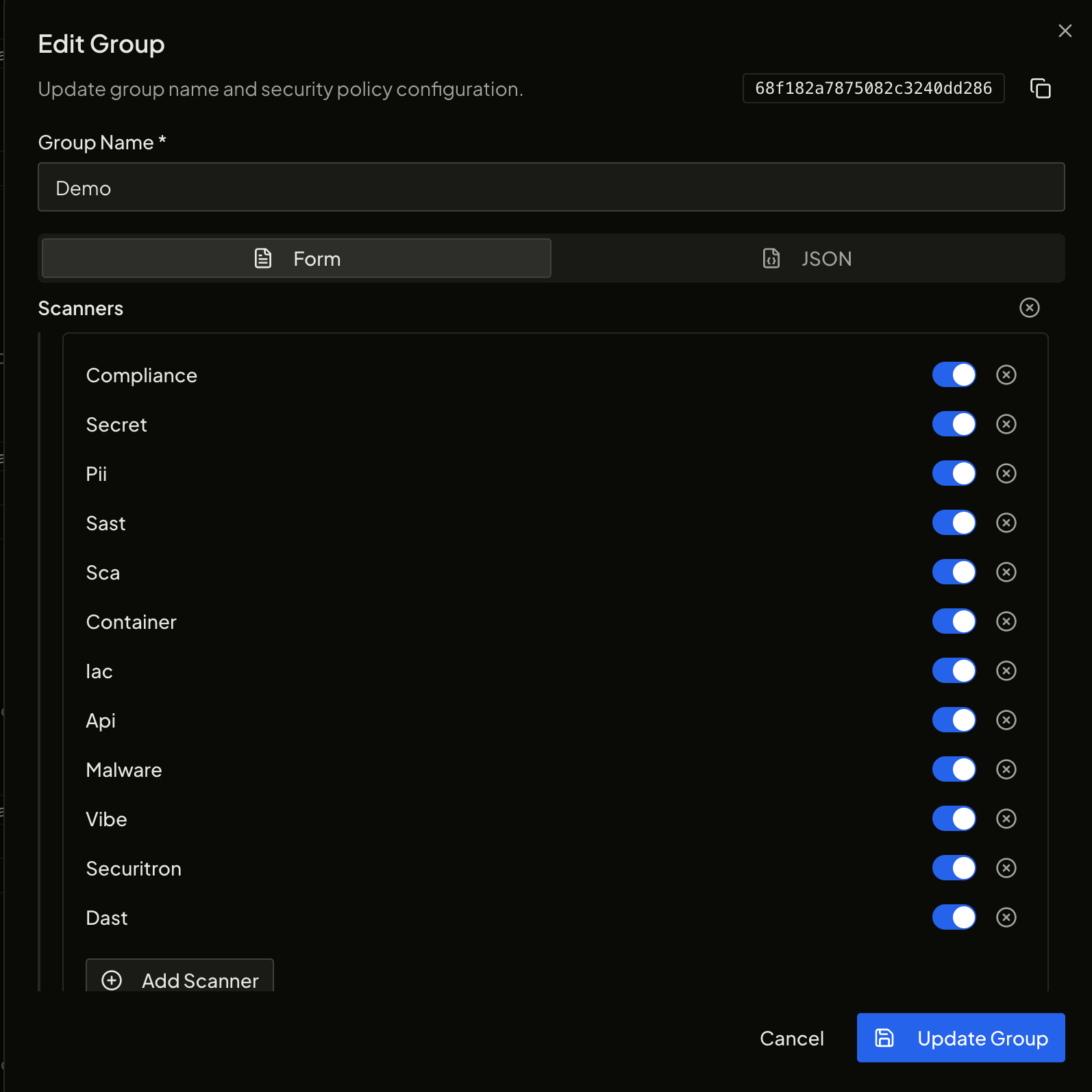
You can now configure your Security Policy directly at the group level without dealing with raw JSON.
Each section is available as a simple, structured form, making updates much easier and more readable.
Give it a try — enjoy the smoother workflow!
November 14th, 2025
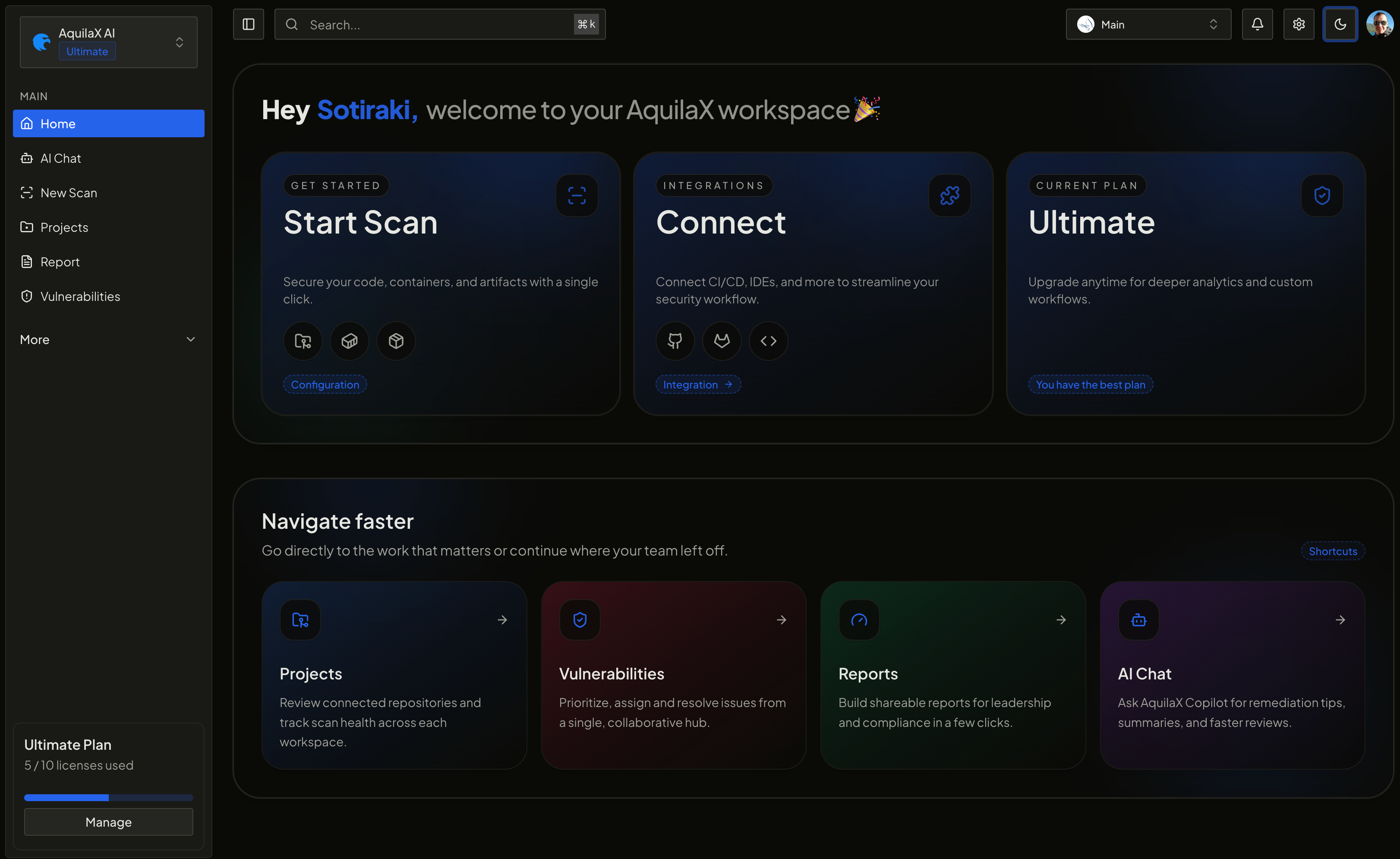
We’ve rolled out a new landing page for the AquilaX Dashboard to all users.
The updated layout simplifies navigation, improves structure, and offers a more modern, intuitive interface.
Nothing to configure on your side — just log in and explore the cleaner workflow.
Enjoy!
November 14th, 2025
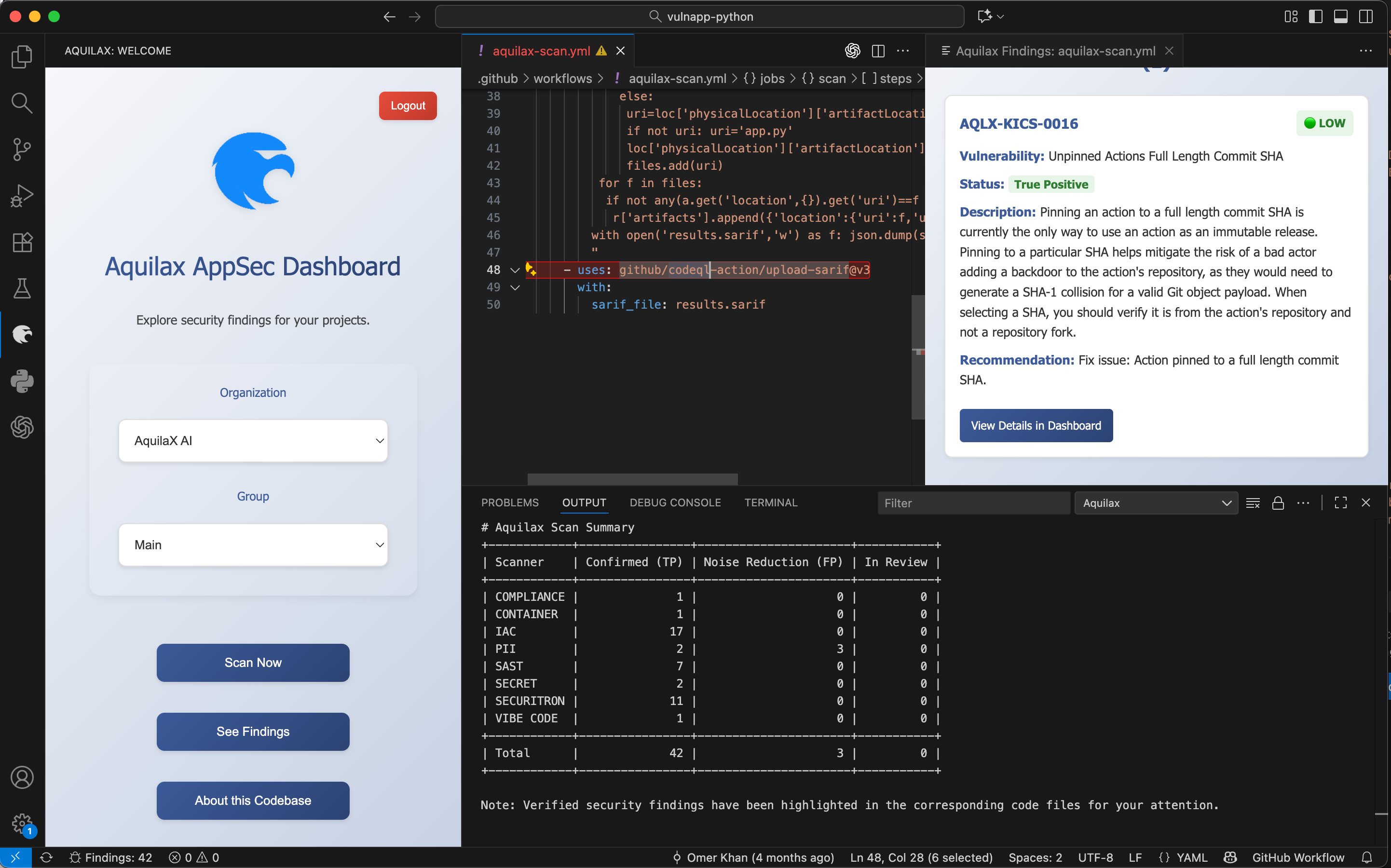
We’re excited to announce a new version of the AquilaX VS Code extension, designed to make secure coding even easier and more intuitive.
🔍 Real-Time Vulnerability Detection
Security issues are now highlighted inline as you write code, helping you catch problems instantly.
🔗 Integration with AquilaX Scans
Your scan results from the AquilaX platform are automatically synced and mapped to the exact file and line where issues appear.
📘 Detailed Insights
See severity, descriptions, and recommended fixes directly inside VS Code—no need to switch tools.
⚡ Simple Setup
Install the extension and connect it with your AquilaX account in just a few minutes.
Documentation:
https://docs.aquilax.ai/user-manual/devtools/ide/vs-code
August 8th, 2025
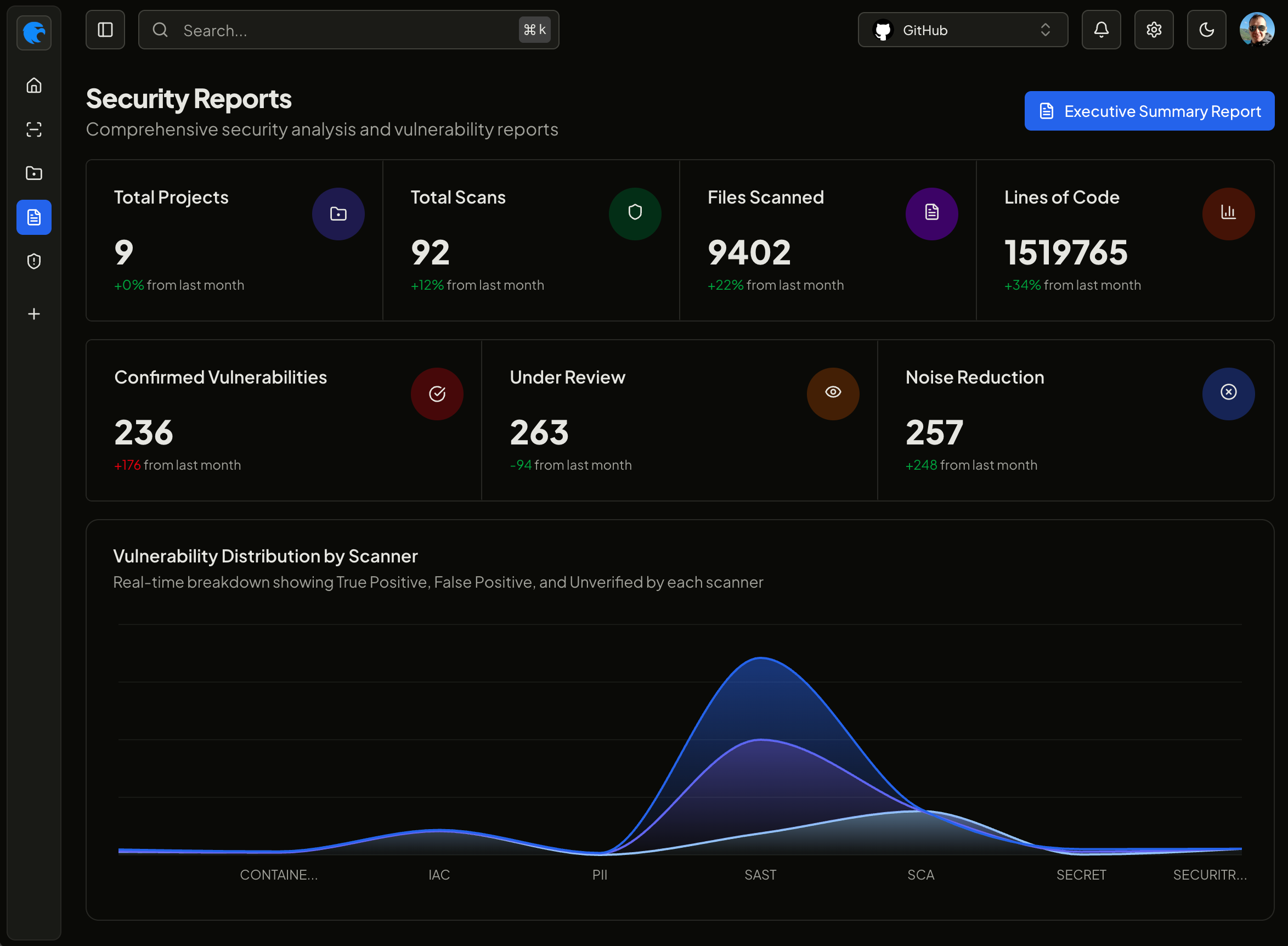
We’re thrilled to announce the rollout of a brand-new UI for AquilaX!
Expect a cleaner, faster, and more intuitive experience designed to boost productivity and reduce clicks (and headaches).
🔧 What’s New?
Sleek new layout for easier navigation
Improved accessibility and responsiveness
Dark mode that actually respects your retinas
Streamlined workflows for common actions
📌 What Didn’t Change?
All existing APIs remain the same.
No changes required on your end — your integrations and automation scripts will continue to work as expected.
Explore the new experience now at https://aquilax.ai
July 21st, 2025

📅 Release Date: 21 July 2025
Affected Endpoints:
GET /api/v2/vulnsGET /api/v2/scan/:scan_id
🆕 What’s Changed:
We’ve simplified the structure of the response payload for the endpoints listed above by removing the results array and introducing a flattened findings array instead.
✅ Benefits:
Easier to parse – You no longer need to loop through nested
resultsobjects.Cleaner output – All relevant vulnerability information is now directly accessible in a single array (
findings).Improved performance – Smaller payloads and fewer nesting levels.
📦 Before (Old Structure)
{
"results": [
{
"scanner": "sast",
"findings": [
{
"id": "...",
"vuln": "...",
"severity": "...",
...
}
]
}
]
}🚀 Now (New Structure)
{
"findings": [
{
"id": "...",
"scanner": "sast",
"vuln": "...",
"severity": "...",
...
}
]
}🔧 Action Required:
If you’re consuming these APIs, please update your client-side logic or integrations to expect a flat findings array instead of nested results.findings.